|
|
8 gadi atpakaļ | |
|---|---|---|
| .github | 7 gadi atpakaļ | |
| Documentation | 7 gadi atpakaļ | |
| backend | 7 gadi atpakaļ | |
| dist | 7 gadi atpakaļ | |
| logos | 9 gadi atpakaļ | |
| network | 8 gadi atpakaļ | |
| pkg | 7 gadi atpakaļ | |
| subnet | 7 gadi atpakaļ | |
| vendor | 8 gadi atpakaļ | |
| version | 9 gadi atpakaļ | |
| .dockerignore | 8 gadi atpakaļ | |
| .gitignore | 8 gadi atpakaļ | |
| .travis.yml | 8 gadi atpakaļ | |
| CONTRIBUTING.md | 10 gadi atpakaļ | |
| DCO | 10 gadi atpakaļ | |
| Dockerfile.amd64 | 8 gadi atpakaļ | |
| Dockerfile.arm | 8 gadi atpakaļ | |
| Dockerfile.arm64 | 8 gadi atpakaļ | |
| Dockerfile.ppc64le | 8 gadi atpakaļ | |
| Dockerfile.s390x | 8 gadi atpakaļ | |
| LICENSE | 10 gadi atpakaļ | |
| MAINTAINERS | 8 gadi atpakaļ | |
| Makefile | 8 gadi atpakaļ | |
| NOTICE | 10 gadi atpakaļ | |
| README.md | 7 gadi atpakaļ | |
| bill-of-materials.json | 7 gadi atpakaļ | |
| bill-of-materials.override.json | 7 gadi atpakaļ | |
| glide.lock | 8 gadi atpakaļ | |
| glide.yaml | 8 gadi atpakaļ | |
| license-check.sh | 8 gadi atpakaļ | |
| main.go | 7 gadi atpakaļ | |
| packet-01.png | 10 gadi atpakaļ |
README.md
flannel
Flannel is a virtual network that gives a subnet to each host for use with container runtimes.
Platforms like Kubernetes assume that each container (pod) has a unique, routable IP inside the cluster. The advantage of this model is that it reduces the complexity of doing port mapping.
How it works
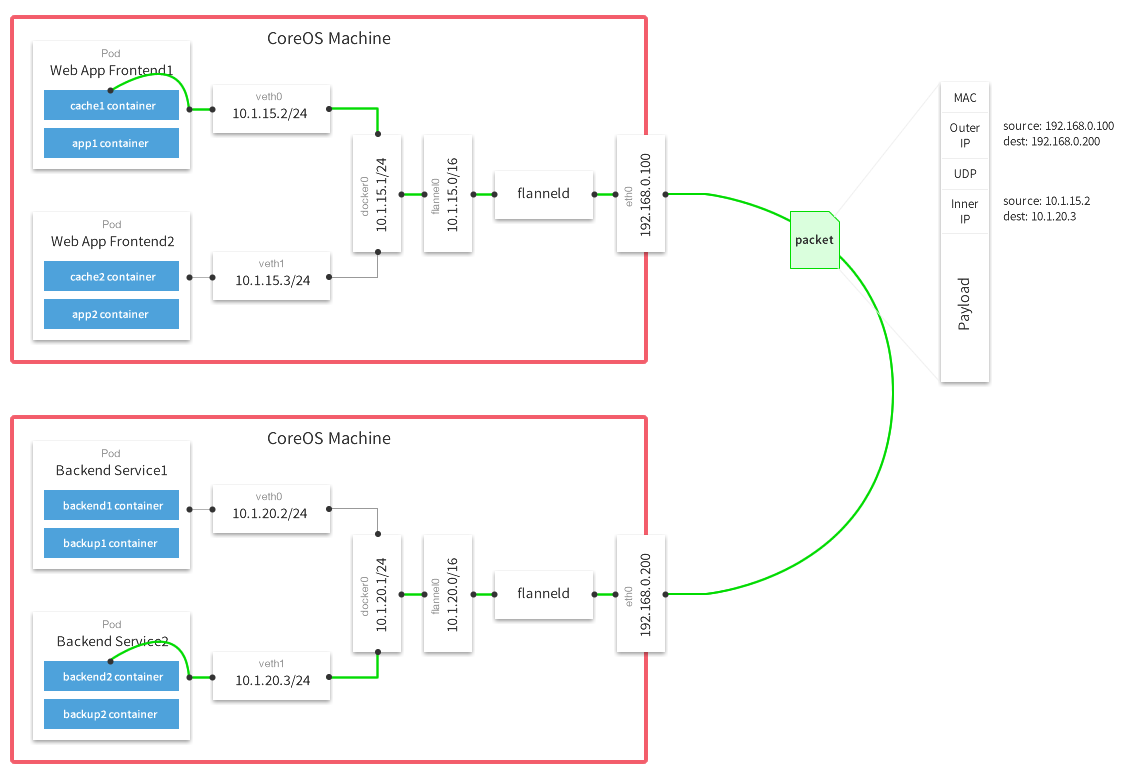
Flannel runs an agent, flanneld, on each host and is responsible for allocating a subnet lease out of a preconfigured address space. Flannel uses either etcd or the Kubernetes API to store the network configuration, allocated subnets, and auxiliary data (such as host's IP). Packets are forwarded using one of several backend mechanisms.
The following diagram demonstrates the path a packet takes as it traverses the overlay network:
Getting started
The easiest way to deploy flannel with Kubernetes is to use one of several deployment tools and distributions that network clusters with flannel by default. CoreOS's Tectonic sets up flannel in the Kubernetes clusters it creates using the open source Tectonic Installer to drive the setup process.
Flannel can use the Kubernetes API as its backing store, meaning there's no need to deploy a discrete etcd cluster for flannel. This flannel mode is known as the kube subnet manager.
Adding flannel
Flannel can be added to any existing Kubernetes cluster. It's simplest to add flannel before any pods using the pod network have been started.
For information on deploying flannel manually, using the (currently alpha) Kubernetes installer toolkit kubeadm, see Installing Kubernetes on Linux with kubeadm.
Using flannel
Once applied, the flannel manifest defines three things:
- A service account for
flannelto use. - A ConfigMap containing both a CNI configuration and a
flannelconfiguration. The network in theflannelconfiguration should match the pod network CIDR. The choice ofbackendis also made here and defaults to VXLAN. - A DaemonSet to deploy the
flannelpod on each Node. The pod has two containers 1) theflanneldaemon itself, and 2) a container for deploying the CNI configuration to a location that thekubeletcan read.
When you run pods, they will be allocated IP addresses from the pod network CIDR. No matter which node those pods end up on, they will be able to communicate with each other.
Kubernetes 1.6 requires CNI plugin version 0.5.1 or later.
Documentation
- Building (and releasing)
- Configuration
- Backends
- Running
- Troubleshooting
- Projects integrating with flannel
- Production users
Contact
- Mailing list: coreos-dev
- IRC: #coreos on freenode.org
- Planning/Roadmap: milestones, roadmap
- Bugs: issues
Contributing
See CONTRIBUTING for details on submitting patches and the contribution workflow.
Reporting bugs
See reporting bugs for details about reporting any issues.
License
Flannel is under the Apache 2.0 license. See the LICENSE file for details.